CYBER THREAT ARTICLE - RANTINGS OF A CYBER SECURITY ANALYST (NOVEMBER EDITION)
Rantings of a Cyber Security Analyst - (November Edition)
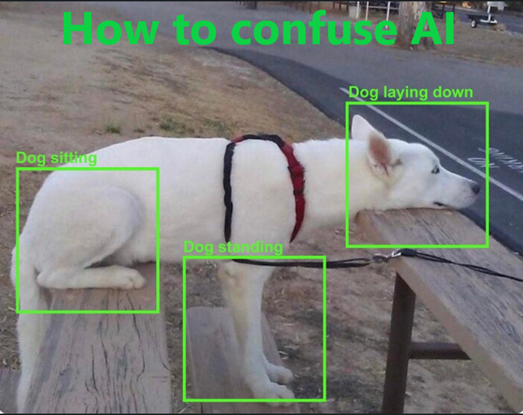
I recently saw someone post this and funny as it is, it does make sense. As a human, what would
be your answer to this?
How would you describe what is the dog doing?
Till today, I still experience companies with misconceptions that Machine Learning
solves ALL cyber security problems. I am not saying such technologies are useless;
they do help a lot by doing pattern recognition and quick decision making based on known
behaviours and other more time-consuming activities.
In my opinion, Machine Learning is essential in today’s threat landscape,
but it does not completely eliminate threats. Look at all security vendors today and
tell me which one does not use some form of Machine Learning? Look at the news and look
at the companies that were reportedly breached. I am sure they use most of these
vendors for their security.
As discussed in my previous write-up, cyber threats are growing because: -
- Businesses need to be online; more services are exposed on the internet.
- There will always be ways to exploit weakness on systems (vulnerabilities, human error, etc).
- Risk for cyber criminals is lower than physical crime (compared to physically breaking into a company).
- Unfortunately, cybercrime is profitable.
Machine learning requires some form modeling. By collecting samples and using algorithms
to “train” the engines, security products can block new and unknown malicious threats.
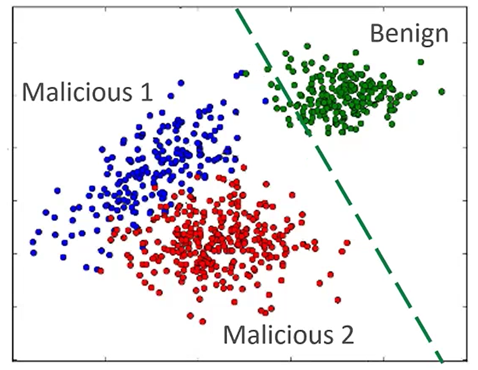
However, like you and I in our daily lives, when we encounter issues, we will think of ways to
overcome these difficulties to achieve our goals. Threat actors have a goal of breaching your
environment.
Just as we go about looking for solutions to overcome difficulties, so do threat actors.
Machine Learning cannot predict the future like a crystal ball. It is created by humans and
needs to
have “seen” examples of the data for reference. Threat actors know this and have ways to evade
detections. In fact, threat actors also use Machine Learning,
like automating the gathering of IT assets of the victim’s environment.
I was asked about playbooks and felt there are misconceptions about them. Usually in Security
Orchestration Automation & Response systems (SOAR), there are playbooks.
Most come with pre-configured playbooks as recommendations.
Playbooks are plans developed that outlines steps taken in the event of a security incident.
They are not fixed and should be developed based on the needs and policies of the company.
Questions like “please share your playbooks for comparison with another vendors” does not make
sense.
They are guidelines and should be further developed by the organizations. If guidance is
required,
it should be a discussion between the company and security vendor to develop the playbooks that
matches the policies and needs of the company. Unfortunately, SOAR with the playbooks can only
automate responses
which can be identified as true positive by the logics configured. As mentioned above, threat
actors can and will use methods to evade or cause uncertainties which the automated solutions
cannot make conclusive decisions. That is where alerting the security team comes in useful. The
saying “It takes a thief to catch a thief” holds true.
For those interested in reading more about Machine Learning and AI, I recommend reading the
articles by Alex Polyakov.
His write-up on this topic is detailed and purely talks about AI concepts without the marketing
fluff.
https://medium.com/towards-data-science/search?q=alex+polyakov
Biography
Harvey Goh

Harvey Goh is a cyber security specialist having been in the cyber security industry for over 15
years as technical personnel. Currently he is working as part of Sophos’ Managed Threat Response
team. He is also a member of AiSP CTI SIG, EXCO and volunteer at CSCIS CTI SIG.
Views and
opinions expressed in this article are my own and do not represent that of my places of work.
While
I make every effort to ensure that the information shared is accurate, I welcome any comments,
suggestions, or correction of errors.