CYBER THREAT ARTICLE - RANTINGS OF A CYBER SECURITY ANALYST (AUGUST EDITION)
Rantings of a Cyber Security Analyst - (August Edition)
Disclaimer, for any marketing people reading this article, please note I am not specifically
targeting anyone. These are just my personal views and I hope to shed some light, which I hope
would
make everyone’s cyber security journey better
AI, Machine Learning, Automation… the list of trend words goes on. I am not a salesperson, have
never seen myself as one. As a technical person, all I want is a feasible solution to solve
problems. Often, we hear lots of buzz words and how they can magically prevent attacks. The
continuous write ups about how Product A can stop ransomware.
Are they lying? No. I
genuinely
believe every vendor has come up with unique ways to identify behaviours of a ransomware. Mind
you,
this is no easy feat as encryption is a legitimate process. Think of device encryption,
encrypting
your own files for secure storage or transmission. Ransomware behaves the same way and to
identify
which is legitimate and which is not poses a tough challenge.
So why do I bring up this topic you may ask? I have seen many cases of companies being hit with
ransomware and their immediate thought is that the product has failed them. I have even
encountered
a company that has changed their endpoint security vendor three times over a course of a few
years,
each due to a ransomware attack.
I am sure the conversation went like this: -
- Local IT Team: We got hit with ransomware, Product A failed us! They told us they can prevent ransomware attacks!
- Product B Sales: Our product can protect you against ransomware! (Pulls out Gartner and some other research article to back their claims).
- Local IT Team: Ok, let’s change to Product B.
- *Few months or years later, another ransomware incident occurs*
- Local IT Team: Product B failed us! They said they can prevent ransomware attacks!
- Product C Sales: We have the best ransomware protection in the market! (Again, pulls out Gartner and other research articles)
- *The cycle continues*
Now, is it true that all products failed? Did all the marketing, research articles lie to us?
Being
a threat analyst, I looked at these attacks and find that in most cases, these products will
block
the payloads used by the threat actor. So how, you may ask, did the ransomware still
occur?
One important thing that I feel all these hype about ransomware attacks failed to talk about is
that
these are humans that have trained themselves to overcome security controls in as short amount
of
time as possible.
It is no longer a case of someone within the office accidentally clicking on a link or
downloading a
file. We are at an age where threat actors are putting in effort to understand how different OS
works, what tools are available to them, how to obtain access and privileges. Noticed I never
mentioned anything about improving their ransomware payload. These skills allow them to quickly
identify security gaps, granting them permissions to shut off or overcome security products, or
find
a machine that has weaker controls. Some of these groups even proudly advertise they are testing
your security controls.
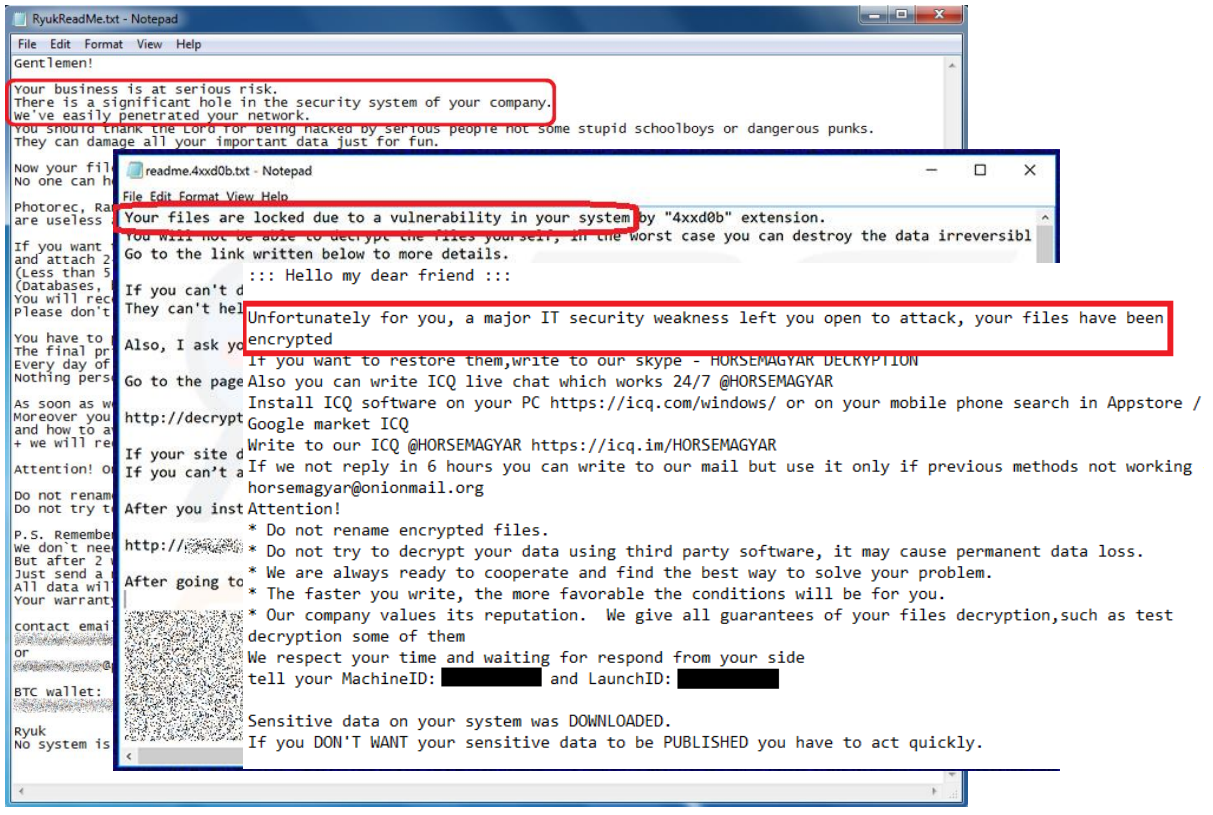
I am not advocating ransomware groups, but those who got breached needs to acknowledge the truth
in
the highlighted statement above. Bear in mind, they referenced security system, not a specific
product.
In a ransomware attack, I would like to say the ransomware is the end result,
but it
is the breach we should be concern about. Everyone seems to be so focused on the end result of
seeing encrypted files that many failed to even consider breach prevention or detection. It just
so
happens that having the end result of ransomware draws the most profit for the threat groups
now,
but with a breach of an environment, the threat actor is free to do anything they wish.
You can buy the best gate, marketed as being hard to cut though with saws or any other tools,
with a
lock that has been advertised as unpickable but left a key hidden under the floor mat for
convenience. If your house gets broken into because someone saw you place the key there, would
you
say the lock or gate failed you?
So, the answer is no, the marketing and sales did not
lie
to you, they just answered the specific question of “Can your product prevent ransomware” which
they
are not wrong for answering yes.
Maybe it is time the security teams step up to design
and
determine the requirements to secure their networks and not just follow trends and asking vague
requirements.
Biography
Harvey Goh

Harvey Goh is a cyber security specialist having been in the cyber security industry for over 15
years as technical personnel. Currently he is working as part of Sophos’ Managed Threat Response
team. He is also a member of AiSP CTI SIG, EXCO and volunteer at CSCIS CTI SIG.
Views and
opinions expressed in this article are my own and do not represent that of my places of work.
While
I make every effort to ensure that the information shared is accurate, I welcome any comments,
suggestions, or correction of errors.